All People Seem To Need Data Processing is not only a fact of life, it’s also a mnemonic to help computer network technicians remember the OSI model and help isolate problems when troubleshooting networks.
Even though the OSI model utilizes the TCP/IP protocol, the model was originally designed by the Open Systems Interconnection group to promote the OSI protocol in its attempt to create a standardized network architecture for network communications. Unfortunately, though the OSI protocol supported more virtual addresses, its complexity made the TCP/IP protocol the more popular choice among network technicians. Ironically, the simplicity of the TCP/IP protocol has led to IPv4 address exhaustion and its newer IPv6 protocol very much resembles the original OSI protocol in complexity.
This step by step guide to the OSI model explains the 7 layers that make up computer networking using the rather well known process of ordering a pizza.
Application Layer
The application layer is the user interface that internet users interact with to send or receive data through email, online games, peer to peer file transfer, and other applications.
Clicking on a link on an internet browser is akin to a customer dialing on their phone to order a pizza.
Common protocols associated with the application layer: Hypertext Transfer Protocol (HTTP), Hypertext Transfer Protocol Secure (HTTPS), Telnet, Secure Shell (SSH), File Transfer Protocol (FTP), Trivial File Transfer Protocol (TFTP), Simple Mail Transfer Protocol (SMTP), Post Office Protocol 3 (POP3), Dynamic Host Configuration Protocol (DHCP), Domain Name System (DNS), Network Time Protocol (NTP)
Presentation Layer
The presentation layer translates the commands received from the application layer into universal, well-known networking formats. Think of the presentation layer as a more effective version of Google Translate but for networks. This is the layer where data encryption and character set conversion occur.
In order for our pizza customer to place an order, she needs to speak a common language with the person taking her order.
Common protocols: Joint Photographic Experts Group (JPEG), Graphics Interchange Format (GIF),(Tagged Image Format File (TIFF), Moving Picture Experts Group (MPEG), American Standards Code for Information Interchange [ASCII], Extended Binary Coded Decimal Interchange Code [EBCDIC], Secure Sockets Layer (SSL), Hyperxt Transfer Protocol (HTTP), HyperText MarkUp Language (HTML), File Transfer Protocol (FTP) AppleTalk Filing Protocols, JAVA
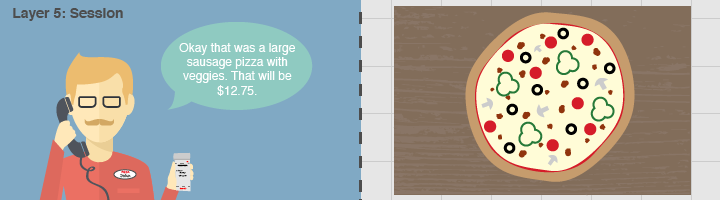
Session Layer
In order for a packet to reach its destination, the session layer establishes a “mechanism for opening, closing and managing a session between end-user application processes and responses”. The session layer makes it possible to establish an open communication line to send the requested packets.
This layer can be compared to making a phone call and having the other person pick up the phone. Without another party on the line, no food-related or network-related conversation would occur.
Common protocols: Lightweight Directory Access Protocol (LDAP) and Remote Procedure Call (RPC), as well as NFS, SQL, and X Windows
Transport Layer
The transport layer not only defines how data is sent, but also provides validation and firewall security.
You can think of the transport layer as quality control. Suspicious packets will not make it past a firewall. Similarly, suspicious looking pizzas will not go out for delivery.
Other Functions:
- Flow control
- Error detection
- Correction
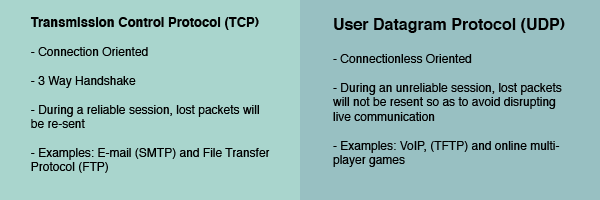
Common protocols: Transmission Control Protocol (TCP), User Datagram Protocol (UDP), Sequenced Packet Exchange (SPX), Name-Binding Protocol (NBP)
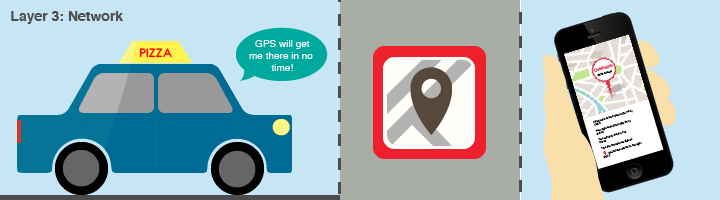
Network Layer
The network layer seeks for the best-known path to route information to reach its destination similar to searching for an address on a GPS.
In the same way that the network layer determines the best way to route information, our pizza deliver person will rely on a GPS to map out a customer’s location.

Common protocols: Routing Information Protocol (RIP), Open Shortest Path First (OSPF), Border Gateway Protocol (BGP)
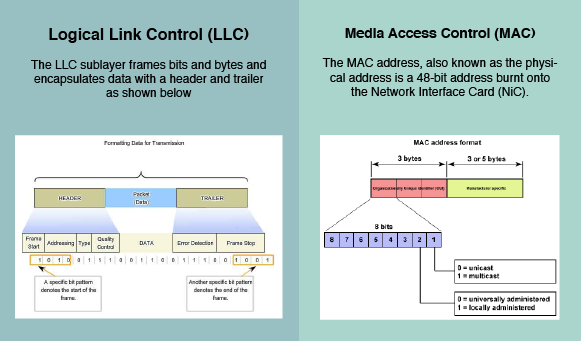
Data Link Layer
The Data Link Layer ensures that a transmission occurs without any errors. The Data Link Layer consists of two sub-layers, Logical Link Control (LLC) and the Media Access Control (MAC), that ensure a successful transmission across different mediums.
One of the major functions of the data link layer is to provide a physical MAC address so that requested information can find its destination. Without a physical address, our pizza delivery man would not be able to complete his delivery.
Preparing network layer packets for delivery:
Common protocols: Ethernet, Token Ring, Fiber Distributed Data Interface (FDDI), and Point-to-Point Protocol (PPP), Frame Relay, and Carrier Sense Multiple Access/Collision Detect (CSMA/CD)
Physical Layer
The physical layer consists of the physical components in a Local Area Network (LAN) such as networking hardware and Ethernet cables. Cabling issues in the physical layer sometimes emerge due to the wrong types of cables (straight through vs. cross over cables) used or faulty cables.
The physical layer comprises of the physical hardware components in a network. In this final step, our now starving customer will receive her delivery.
Common protocols: Fast Ethernet, RS232, and ATM
To learn more about the OSI model click here. If you’re a visual learner, click here.
Don’t forget to follow us on Linkedin, Facebook and Twitter for the latest news in the Telco industry and for other computer information technology resources.