The Fourth Industrial Revolution continues to bring tremendous innovation; it also brings new challenges. These innovations and challenges are most apparent in today’s manufacturing landscape.
Factories worldwide are increasingly shifting to the connectivity of the Industrial Internet of Things (IIoT) to supervise their manufacturing operations more closely. While this digital transformation brings significant efficiencies, it also brings the potential for security risks. Devices with sophisticated operational abilities are a primary target for bad actors looking to attack the global supply chain.
Many major manufacturing companies have been victims of cyberattacks. Here are a few examples:
- The New York-based manufacturer, OXO International, uncovered a breach that took place between June 2017 and October 2018. The company discovered malicious code on its website designed to steal customer data such as payment card information and addresses.
- Visser Precision, a space and defense manufacturing company, suffered a DoppelPaymer ransomware attack around April 2019. This type of ransomware encrypts and removes data and is believed to have originated in Russia. Research of the episode revealed that sensitive non-disclosure agreements with Tesla, SpaceX, and General Dynamics were stolen and published on hackers’ websites. In addition to the non-disclosure agreements, the hack included a schematic for a missile antenna from Lockheed Martin.
- In 2017, the Renault-Nissan company sustained a WannaCry ransomware cyberattack at four of their European plants and one plant in India. All automotive production was halted in these plants for three days at the cost of $400 million.
According to the IBM report entitled X-Force Threat Intelligence Index 2020 :
“Operational technology (OT) attacks surged 2,000 percent year-over-year. Threat actors continue to shift their sights to attack vectors, including IoT, OT, and connected industrial and medical systems.”1
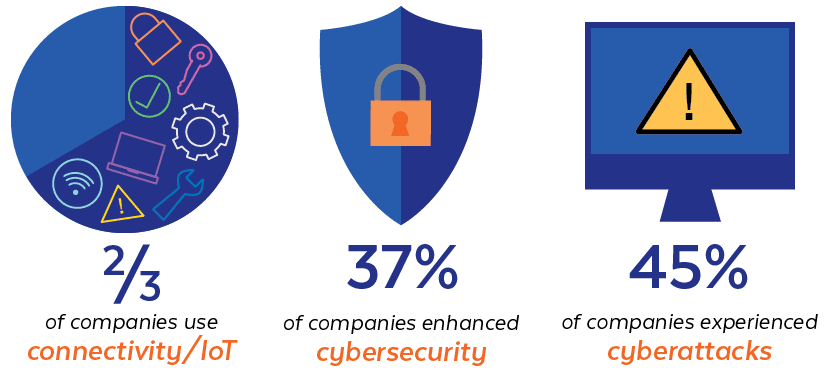
Further, Sikich’s 2020 Manufacturing and Distribution (M&D) Report published the following statistics:
- Two-thirds of the companies in their study reported the use of connectivity/IoT.
- Thirty-seven percent of the companies took a variety of actions to enhance cybersecurity.
- Forty-five of the companies experienced cyberattacks within the last 12 months.2
 Industrial IoT Threats
Industrial IoT Threats
The IIoT has markedly improved the service delivery and productivity of industrial enterprises. It is also true that anything connected to the internet is susceptible to cyber threats. Some of the most vulnerable operating systems include:
- Industrial control systems (ICS)
- Programmable logic controllers (PLC)
- Supervisory control and data acquisition (SCADA)
- Human-machine interfaces (HMI)
Cyberattacks That Focus on IIoT Infrastructure
- Man-in-the-middle: Attackers place themselves into communications between two systems. In an industrial setting, the goal could be to control a smart actuator, knock an industrial robot out of its lane, or change its speed limit, damaging an assembly line and even injuring workers.
- Device hijacking: Simply put, the attacker takes control of a device. For example, a hijacker takes control of a meter and uses it to launch ransomware attacks against an Energy Management System (EMS) or siphon unmetered power lines.
- Distributed Denial of Service (DDoS): This type of attack shuts down a machine or network by inundating it with traffic. DDoS attacks can affect a broad range of IIoT devices, causing severe disruptions to the factory floor.
- Permanent Denial of Service (PDoS): A PDoS attack damages the target device so severely that it needs replacement. An example of this type of malware is BrickerBot—used to exploit hard-coded passwords in IoT devices—which disables vital equipment on a factory floor.
Securing IIoT
IIoT infrastructure should be simple, workable, and, of course, secure. Security solutions should include the following:
Secure Boot
Secure boot is a security mechanism that only uses cryptographic code signing techniques to ensure that a device executes code generated by its original equipment manufacturer (OEM) or another trusted party. This technology subverts attacks by preventing hackers from replacing firmware with malicious instruction sets. It is important to note that not all IIoT chipsets come with secure boot; therefore, it may be necessary to make sure an IIoT device communicates with authorized services.
Mutual Authentication
Mutual authentication, also called two-way authentication, ensures that data originates from a legitimate device. With this process, both the device and service must exchange and verify each other’s identity.
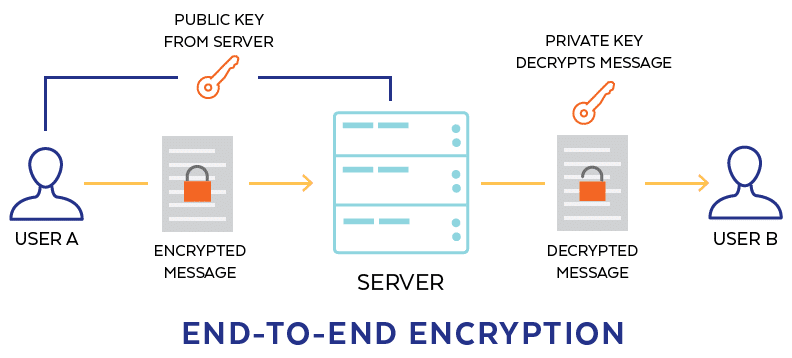
End-to-End Encryption
Data that travels between a device and the cloud must be secure. The utilization of encryption ensures that only those with a decryption key can access transmitted data. For example, a smart actuator sending data to the SCADA must be able to prevent eavesdropping.
Security Monitoring
Security monitoring involves surveilling the general state of an industrial system—particularly endpoint devices and connectivity traffic. Data is collected and then analyzed to expose potential security threats. Should a threat be detected, a wide range of actions are initiated, such as revoking device credentials or quarantining an IoT device. This automatic monitor-analyze-act cycle can happen in real-time or at a later date.
Lifecycle Management
A lifecycle management program focuses on the critical technology in an industrial setting. It identifies outdated operational devices that are not capable of being updated or secured. It allows a manufacturer to know when devices are at the end of their lifecycle and need to be replaced. An essential part of lifecycle management involves secure device decommissioning, which makes sure devices cannot be repurposed and connected to a service without authorization.
Building Cybersecurity in the Smart Factory
Sid Snikin, vice president of cybersecurity for ARC Advisory Group, told the EE Times:
“Everyone wants access to everything: devices and data stores and applications in the cloud. The whole idea is to leverage this connectivity of devices to do new things you haven’t even thought of yet. But all these connections are opening up new security holes, which can mean potentially compromised operations because from a security perspective, you don’t know where data is coming from or where it’s going to on the other end.”3
According to Justin Fier, director of cyber intelligence and analytics at Darktrace:
“Before implementing Industry 4.0 technologies, you need to know what the security ramifications are. But we tend to deploy Industry 4.0 technologies first, and then security as an afterthought.”4
As IIoT devices continue to populate the factory floor, cyber risk will continue to increase. Manufacturing enterprises must embrace an integrated cyber management program that involves both OT and IT in the identification, protection, response to, and recovery from cyberattacks.
According to Deloitte US, here are some steps to consider taking when building an effective cybersecurity program:
- Perform a cybersecurity maturity assessment
- Establish a formal cybersecurity governance program that considers OT
- Prioritizes actions based on risk profiles
- Build in security5
Interested in learning more about LED lighting system security? Click here.
______________________________________
1 IBM: X-Force Threat Intelligence Index 2020
2 Sikich: 2020 M&D Report
3 EE Times: AI on the Factory Floor Challenges Cybersecurity
4 EE Times: AI on the Factory Floor Challenges Cybersecurity
5 Deloitte: Cybersecurity for Smart Factories